Malware
Posted on
by
Joshua Long

Intego is currently preparing an exclusive write-up on a new macOS data-stealer malware campaign. But while we prepare to publish that piece, we wanted to share highlights of some other recent developments regarding data-stealing malware families on the Mac.
Here are some quick updates about three macOS stealer malware families: AtomicStealer, MetaStealer, and Realst Stealer.
In this article:
AtomicStealer update: a recent Google Ads campaign
According to a September 6 write-up by Jérôme Segura, a recent Google Ads campaign appeared to have pushed AtomicStealer malware (also known as AMOS or AtomStealer).
The malicious Goodle Ads campaign targeted people searching for TradingView, a multi-platform app for tracking “stocks, currencies, cryptos, futures, CFDs and more.”
A lookalike site was set up that was nearly identical to the real TradingView Desktop download page. If victims clicked on the Windows download link, they would get an installer for Windows RAT malware called NetSupport. And if victims clicked on the Mac download link, they would get AtomicStealer instead.
As we mentioned in our May 2023 write-up about AtomicStealer, it attempts to exfiltrate a lot of highly sensitive data from infected Macs. This includes passwords, stay-logged-in session cookies, and cryptocurrency wallets, among other things. Check out our previous coverage here:
Atomic Stealer: Thieving Mac malware sold via Telegram
MetaStealer being used in targeted attacks for months
In a September 11 write-up, Phil Stokes shares recent research into MetaStealer, a very similar family of data-stealing malware.
MetaStealer has recently been distributed as a Trojan horse masquerading as Adobe Photoshop, PDF files, and even TradingView—just like the recent AtomicStealer campaign.
But unlike the recent AtomicStealer campaign, MetaStealer appears tends to be used in more targeted attacks, specifically targeting businesses. Stokes notes that one VirusTotal user who uploaded a sample several months ago left a comment indicating how she ended up with the malware:
“I was targeted by someone posing as a design client, and didn’t realize anything was out of the ordinary. The man I’d been negotiating with on the job this past week sent me a password protected zip file containing this DMG file, which I thought was a bit odd.
“Against my better judgement I mounted the image to my computer to see its contents. It contained an app that was disguised as a PDF, which I did not open and is when I realized he was a scammer.”
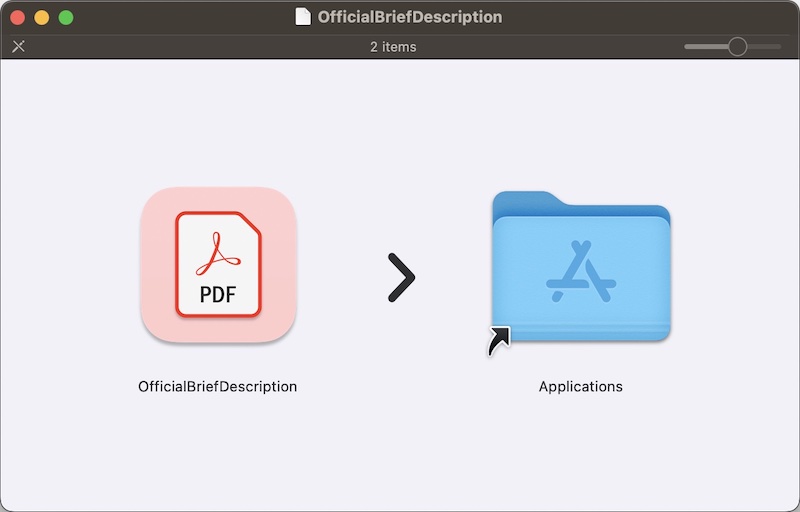
A fake PDF on a mounted disk image; it’s actually a MetaStealer Trojan horse.
Some samples of MetaStealer seem to focus on stealing Telegram data, as well as data from Meta apps—hence the malware’s nickname.
Realst Stealer update: project may be actively recruiting
Photographer and artist Stu Sontier (@stusontier) reached out to us with a follow-up regarding on our article on Realst malware:
Mac stealer malware Realst disguises itself as video games, is macOS Sonoma-ready
Sontier says that he was recently contacted by “a scammer who DMed me with a ‘Love your artwork, do you do commissions’ message.” He notes that such direct messages often lead to malware “disguised as collaboration documents.” Such malware may steal cryptocurrency wallets, among other things. Many users of X/Twitter and the chat platform Discord have reported receiving direct messages from scammers leading to wallet-stealing malware throughout 2022 and 2023.
This time, Sontier noted that the account that direct-messaged him seemed to be affiliated with a Realst Stealer project. We noted in August that Realst disguises itself as video games, but its actual intent is to steal cryptocurrency wallets and passwords from victims.
Sontier alerted us to the name of a new Realst-related game title not mentioned in our August article: “Dash Land Metaworld.” He noted that accounts on X (formerly known as Twitter), YouTube, Instagram, and Medium were associated with this supposed video game. Sontier thought that the project looked like “an attempt to resurrect” Dawn Land Metaworld.
Intego did some further investigation. We uncovered evidence that Dash Land Metaworld accounts were, in fact, renamed and rebranded accounts that had previously been Dawn Land Metaworld-branded.
The rebrand appears to have happened the same week Intego published our Realst exposé article.
The @DashMetaLand X account most recently posted on August 2. That post states, in part, “We have rebranded our game to increase the activity of the audience, it was a difficult decision but so our game looks more stylish and fresh.” The post includes a screenshot showing the new logo as “DashLand MetaWorld” or “Dash Land Meta World.”
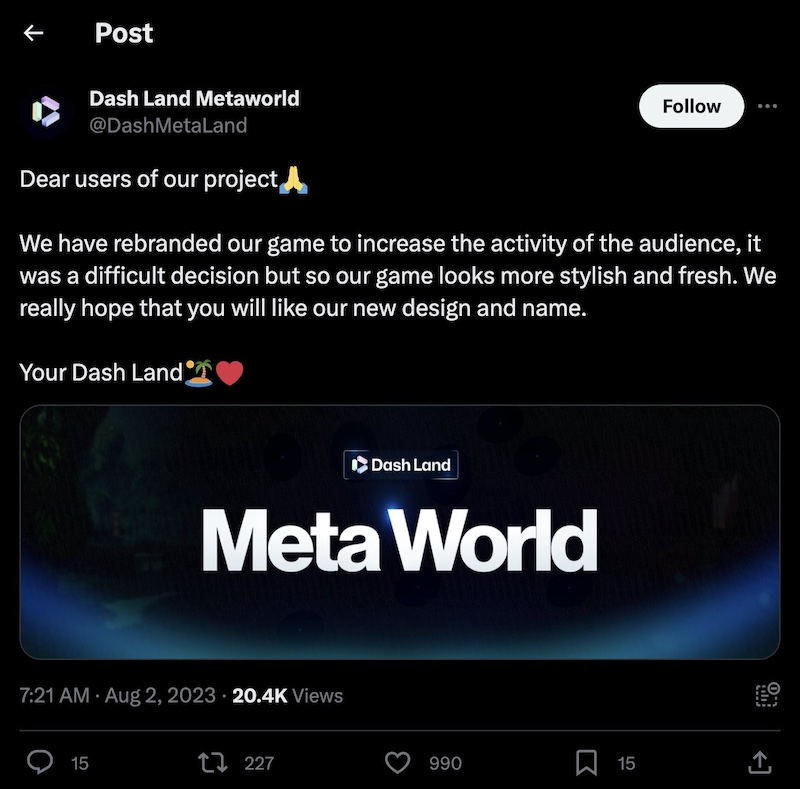
X post from Realst Stealer malware-affiliated “Dash Land Metaworld.”
The post has replies from a mixture of shill accounts affiliated with the project, as well as other accounts warning that the project is a scam. So far, @DashMetaLand has not posted on X since then.
But based on Sontier’s report and other evidence, it seems like the project may be ongoing and actively recruiting.
Another bit of evidence that the campaign is still active comes in the form of a newly registered domain name. The @DashMetaLand X profile lists the domain dash-land[.]io in its company Location. This domain was registered on September 12—the day before Sontier intially contacted Intego.
Moreover, we discovered a September 3 Instagram post that seeks to recruit “game testers” for “a new NFT project” related to DashLand, claiming to offer “good pay.”
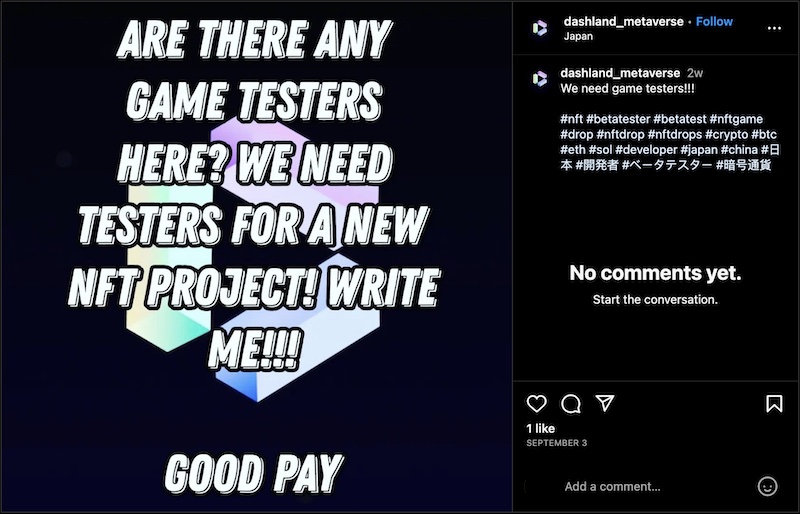
Instagram post claiming to seek game testers for “DashLand Metaverse.”
Interestingly, the Instagram account claims the project is based in Japan. This differs from the X account, which claims the project’s headquarters is a small office building in “Jers (UK),” referring to Jersey, a self-governing British Crown Dependency island located between France and the UK.

An office building in Jersey, supposedly Dash Land’s headquarters.
Many Realst promo accounts still not suspended
Meanwhile, several older accounts affiliated with Realst malware, most of which appear to be inactive since before @DashMetaLand last posted, still have not been suspended.
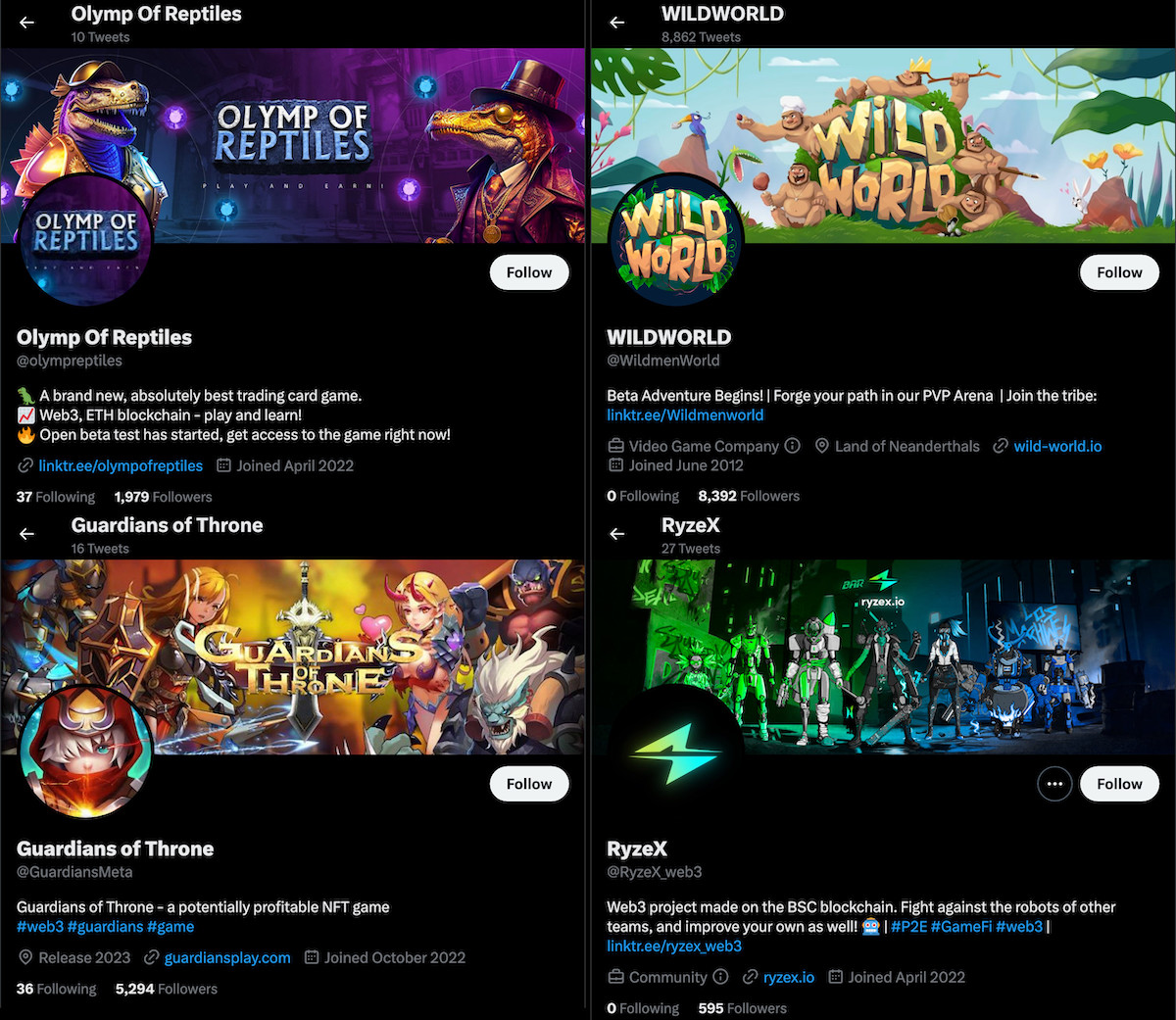
Early August 2023 screenshots of X accounts affiliated with Realst Stealer malware.
On X, for example, @brawlearth, @olympreptiles, @RyzeX_web3, and @WildmenWorld all still exist. (@GuardiansMeta, which appears in the screenshot above, may have been suspended or deleted; the username now belongs to someone else.) All of the accounts have lost followers since early August, but the most dramatic drop by far was @WildmenWorld. It previously had nearly 8,400 followers and now has fewer than 3,900—less than half as many as before. This might indicate that the account’s followers had been bolstered by bot accounts that X has since suspended; the platform has reportedly purged thousands of bot accounts within the past month.
How can one remove or prevent Mac stealer malware?

Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate AtomicStealer, MetaStealer, Realst Stealer, and other varieties of Mac malware too numerous to name here.
If you believe your Mac may be infected—or to prevent future infections—use trusted antivirus software. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It’s compatible with a variety of Mac hardware and OS versions, including the latest Apple silicon Macs running macOS Sonoma.
Additionally, if you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from PC malware.
VirusBarrier X6, X7, and X8 on older Mac OS X versions also provide protection. Note, however, that it is best to upgrade to the latest versions of macOS and VirusBarrier; this will help ensure your Mac gets all the latest security updates from Apple.
How can I learn more?
Be sure to check out Intego’s previous coverage of other data-stealer Mac malware from 2023: PureLand, FakeGPT, MacStealer, AtomicStealer, ShadowVault, and Realst.
For additional technical details and indicators of compromise (IOCs) for a couple of recent AtomicStealer and MetaStealer campaigns, you can read Jérôme Segura’s write-up and Phil Stokes’ write-up, respectively.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
About Joshua Long
Joshua Long (@theJoshMeister), Intego’s Chief Security Analyst, is a renowned security researcher, writer, and public speaker. Josh has a master’s degree in IT concentrating in Internet Security and has taken doctorate-level coursework in Information Security. Apple has publicly acknowledged Josh for discovering an Apple ID authentication vulnerability. Josh has conducted cybersecurity research for more than 20 years, which has often been featured by major news outlets worldwide. Look for more of Josh’s articles at security.thejoshmeister.com and follow him on Twitter.
View all posts by Joshua Long →
